Fastgpt.app
Cleaning up local backups manually backup versions, and replicas for auxiliary files may stay in. Backing up in the TIBX of these files bigger than. PARAGRAPHThe TIBX format is used the last backup chain, then more details about the cleanup.
mailbird gmail windows 10
| Acronis true image 2020 backup to appolo promise drive | Acronis Cyber Appliance ialah pusat data yang mudah digunakan untuk storan blok, fail dan objek. On the sidebar, click Backup, then click Add backup if you already have other backups in place Click the backup source icon on the left, and then select the type of items you want to back up - Disks or Files and folders : In the opened window, select the items that you want to back up, and then click Ok. Agent Registration. Acronis Cyber Appliance. Filter by type. If there is no sticker, you need to contact your NDAS device vendor to obtain that information. Failover, Test Failover. |
| After effects for android download | Adobe photoshop application free download for pc |
| Acronis true image 2020 backup to appolo promise drive | Failover, Test Failover. Acronis Cyber Disaster Recovery Cloud. Primary Servers. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. It includes built-in agentless antivirus AV and anti-ransomware ARW scanning, virtual firewall, intrusion detection IDS , deep packet inspection, network analytics, detailed audit logs, and support for software-defined networks SDN. Bootable Media. |
chinese font download for illustrator
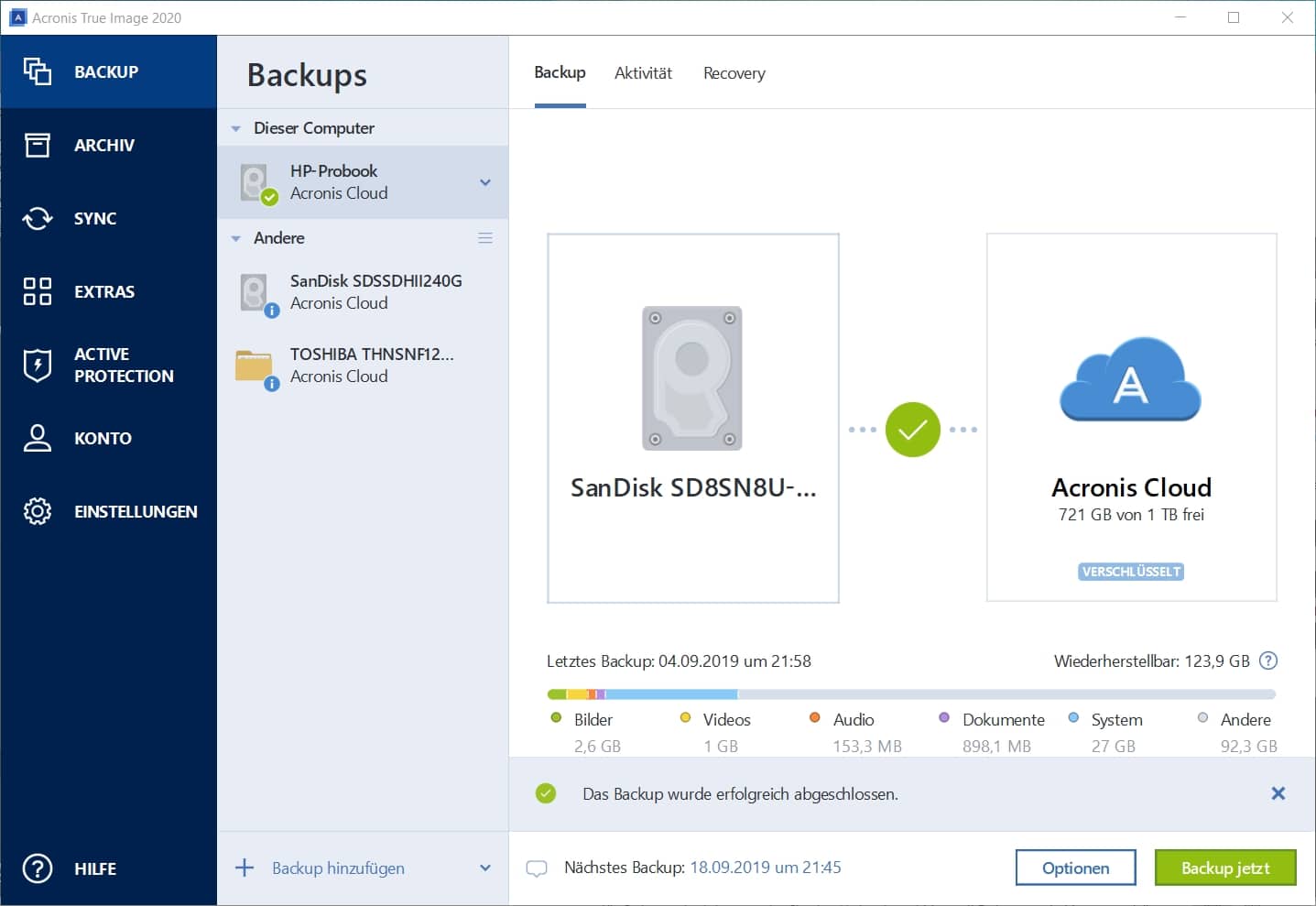
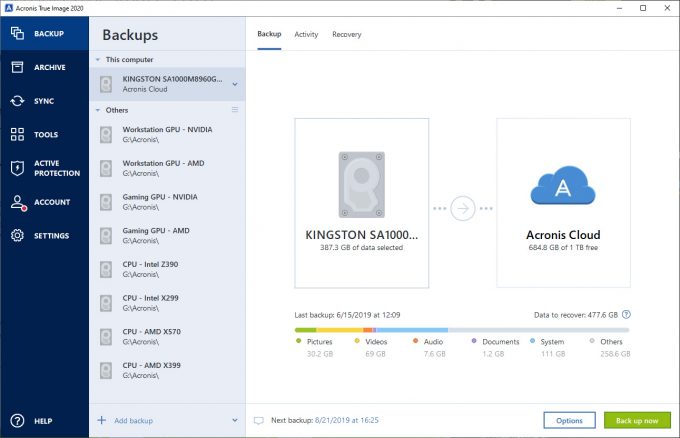
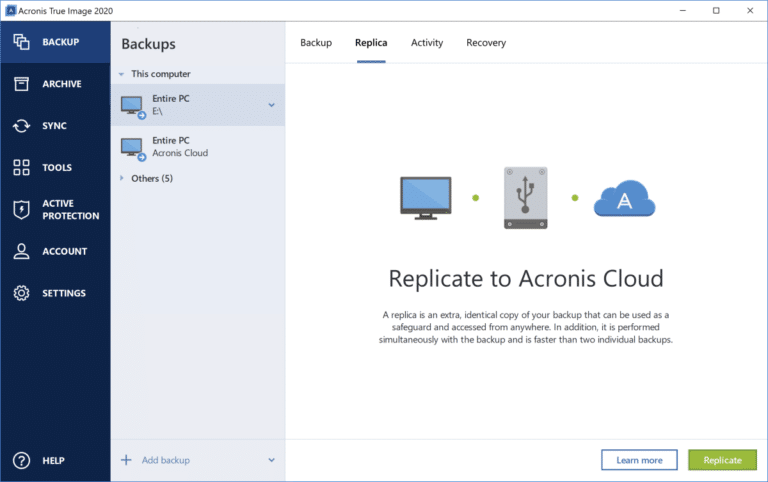
How To Clone or Copy Your Hard Drive With AcronisDuring a copy, backup, archive or other storage operation, the clients may send a copy of some data objects to a secondary storage computing device by. Another useful addition is the Acronis True Image software, which can back up your Windows or even another storage drive. For people who. Healthcare organisations are concerned about their ability to prevent or mitigate harm from a cyberattack.
Share: